Having spent a fortnight in the throes of the Great Game, i.e. on the ethereal fringe that is this Substack, it’s time for something lighter than the bloody mess that is the reality for Palestinians and Israelis.
For my own, mad reasons, I decided in 2012 to write a novel. One of its central themes is the imminent launch of Compliance, a post-national, post-governmental totalitarian state, administered by AI with oversight of all digital events. Its job is to identify anything unusual.
The story references a paper on “adaptive strategies” by the Adaptive Securities and Economics Lab, a research group at the University of Hawaii. Years ago, I designed their website, which appears to be down. The link is to a web-archived version.
The paper simplifies the interaction of two agents, System and Attacker, drawing analogy to the interaction between a biological immune system and a pathogen.
To borrow from my novel:
‘Top brains in cyber went bio decades ago, intrigued by the extraordinary mechanisms that defend the human cell. Cyber was hoping to emulate. First task of an immune system is? Recognise attack. First task of attacker is therefore disguise.’ He levelled a look at me. ‘In order to crack Attacker’s disguise, System must learn while under attack. Meanwhile Attacker must sacrifice disguise in order to learn System’s defence.’ He broke off, perhaps at the faint whooping of sirens from the roundabout below.
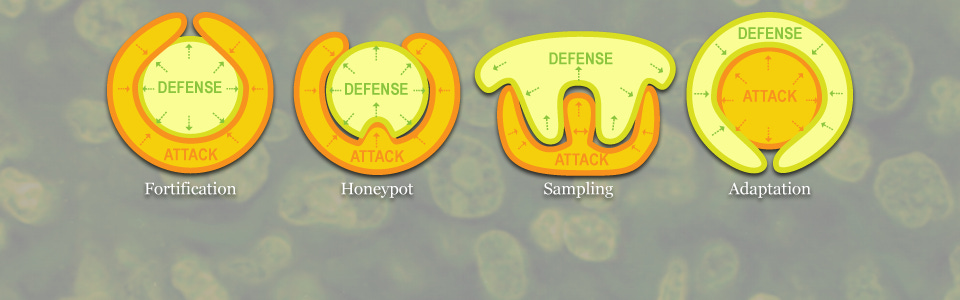
To borrow the diagram I made for AsecoLab:
System (Defense) learns while under attack by shifting from all-out defending on all fronts (Fortification) to allow Attacker in (Honeypot), in order to learn Attackers strategy (Sampling), and turning tables on Attacker (Adaptation).
What we are seeing in the Middle East is precisely this adaptive strategy at work. The model I just outlined is simplistic, and at the same, all we need to know, and at the same time again, all we can know about the machinations of the Great Game.
What? The Middle East again? I did say this piece was a trick of the light
The awful and violent attack on Israeli peacenik ravers and kibbutzim on October 7, including women and children, was immediately condemned as the vile work of Hamas terrorists. “This is Israel’s 9/11,” Gilad Erdan, Israeli ambassador to the United Nations, told an emergency meeting of the Security Council the day after the attack.
The word “terrorist” is important. As I described in my piece, Israel Enemy of the Jews, the UN Commission on Human Rights reports that there is no global consensus on the definition of “terrorism” or “terrorist”.
It became a special word after 9/11. Bush and Blair used it repeatedly to justify “smoking out” Osama Bin Laden from the caves of Tora Bora. When references were made to the Geneva Conventions, Donald Rumsfeld, American Secretary of Defence, and Deputy Paul Wolfowitz, devised a legal definition of “non enemy combatant” they could apply to any target, effectively waiving any subscription to the rules of war. The UK ran with this ball in its own witch hunt for Islamic enemies within.
Chapter Two of The 9/11 Commission Report: Final Report of the National Commission on Terrorist Attacks Upon the United States, published 22 July 2004, just over a year after the USA invaded Iraq, is titled “The Foundation of the New Terrorism.” In its documentation of the rise and fall of Osama Bin Ladin, there is no mention of his connections to the Bush dynasty.
The special word was deployed again to justify the invasion of Iraq on the fake premise that Saddam Hussein had nuclear weapons. David Kelly, the British nuclear scientist charged with locating those nuclear weapons was reported to have committed suicide in July 2003. As with the WMD report, there are doubts.
The Chilcot Enquiry into the UK’s role in the invasion of Iraq, published 2016, condemned the invasion and PM Tony Blair on a number of grounds, including “deliberate exaggeration of the threat posed by Saddam Hussein.” Blair’s response to the report is a masterpiece of triplespeak.
“Terrorist” is a magic spelll. In three syllables, a target is stripped of all rights, from the Geneva Conventions to basic human rights. It grants the user a one-way dynamic, like a gun. Bin Laden was a terrorist. Saddam was a terrorist. The IRA was a terrorist organisation, like Al Qaeda, ISIS and ISIL. Now it is Hamas.
As 9/11 gave the Americans green light to drop a vast tonnage of bombs on Afghanistan, the October 7 attack has given Israel license to drop an even larger tonnage on Gaza, and conduct pre-emptive strikes against targets in the West Bank, Syria and Lebanon.
Let’s apply our adaptive strategies diagram to the mainstream narrative. System is Israel. Attacker is Hamas.
Fortification
Israel defends itself against Hamas via e.g. missile defence system Iron Dome, and high levels of proactive and pre-emptive security in the face of its neighbours, including the Palestinians.
Maintaining this all-out defence is expensive, requiring billions of dollars donated by the USA, UK and other countries, and revenues from the sale of defence systems to those countries. It also requires compulsory military service by Israeli citizens.
Honeypot and Sampling
Rather than defend all fronts, it is more efficient for Israel to create a controlled space for Hamas to operate in, and thereby learn its strategies
Adaptation
The roles of System and Attacker are reversed. Now Hamas must defend on all fronts.
At first, this looks unremarkable, even sensible. Israel has a right to defend itself. In the light of 9/11, the invasions of Afghanistan and Iraq, and the revelations of Julian Assange and Edward Snowden, we must look again.
System and Attacker operate the same adaptive strategy. A pathogen attacking a human cell must disguise itself. It might surrender a fake disguise, knowing that the immune system is trying to spot its disguises. Similarly, System might fake a defence—or go a step further and fake an attack. Where does this get us?
From my novel:
What we have is a game of bluff. Neither side can call it without giving it away. The ensuing dynamics ensure one of two outcomes. Either System learns all Attacker’s disguises or Attacker learns all System’s defences. The first is Compliance. The other is chaos.’ He relaxed suddenly, displaying a warm smile. ‘This is all highly sensitive, of course.’
Chaos is post-truth fog. Everything is spun. Everything is subject to the ceaseless multiplication of bluff. Under these conditions, there is a vanishingly fine line between permitting Attacker to attack, in order to learn its methods and disguises, and facilitating that Attack. To understand 9/11 and October 7, in the context of System’s stated strategies and the immediate and disproportionate response of USA, UK and Israel respectively, we must zoom into this fractal boundary.
We must consider that, once the cellular dynamic of System/Attacker is known, and information sources are controlled, further levels of bluff are available. The adaptive dynamic itself can be faked, or denounced as fake, or the denunciation faked. The truth vanishes.
In an interview on Talk TV, Piers Morgan repeatedly asks British rapper and activist Low Key if he “condemns the Hamas terrorist attack.” Low Key defends his reasons for not answering, first as a refusal to participate in the one-way dynamic of the magic spell. Second he refers to the adaptive strategies of the Israeli military.
According to Mondo Weiss:
There are a growing number of reports that indicate the Israeli military was also responsible for Israeli civilian and military deaths on October 7 and the days after.
Citing eye-witness reports from Kibbutz Be’eri, one of the places attacked on 7 October, that Israeli soldiers “eliminated everyone,” both hostages and attackers, the article asks if the Hannibal Directive was obeyed.
The Hannibal Directive (Hebrew: נוהל חניבעל) (or "Procedure" or "Protocol") is a controversial procedure used by Israeli Defense Forces (IDF) to prevent the capture of Israeli soldiers by enemy forces.
It was introduced in 1986, after a number of abductions of IDF soldiers in Lebanon and the subsequent controversial prisoner exchanges. The full text of the directive has never been published and until 2003 Israeli military censorship even forbade any discussion of the subject in the press. The directive has been changed several times. At one time the formulation was that "the kidnapping must be stopped by all means, even at the price of striking and harming our own forces."[2]
While its reference to the protocol, and examples of its application—e.g. the capture of IDF soldier Hadar Golding in 2014, which prompted an Israeli retaliation that took his life and 130 Palestinians lives—are factual, we must consider that this anonymous article might be fake.
The calculus of bluff and counter-bluff deployed by intelligence services can be extrapolated to encompass the entire mediatised world. Covid-19 is another great example. A virus evolved from a wet market in Hunan? Or a bioweapon? The difference is a fractal boundary.
The situation would be hopeless if the bluffing game were invisible. Fortunately it is easy to spot. Just as a nuclear weapon leaves an obvious trace, so do the verbal weapons “terrorist” or “condemn.” Their deployment is intended to create a one-way dynamic. A wall of truth is erected for us. On one side is System, on the other, Attacker. “You’re either with us or you’re against us,” said George W Bush in his War on Terror.
The Israeli narrative of the Palestine issue is crumbling. Even the T-word cannot save it, except for those who prefer to live within engineered walls of “truth” and turn a blind eye to the light streaming through the cracks.
Many Jews and Israelis insist the same applies to the Palestine narrative. Hamas sites its rocket launchers in schools and hospitals, using civilians as a human shield, and is therefore responsible for their deaths. By existing, Hamas is responsible for the lockdown of Gaza, for infant mortalities on their own side as well as the other.
Systems around the world admire the State Israel for its mastery of the game against Attacker. In the intelligence community, Mossad is feared and respected for its skullduggery. Israel is a world leader in the export of technological systems of surveillance and counter-surveillance.
As the numbers mount—the women, the children, the destruction—in escalating asymmetry, we must think, who is System and who is Attacker? Must we humans continue to play this game, or watch it being played? What else can we do?
Amidst the madness of intellligence, the T-word is a smoking gun. We must decode the motives of the trigger-puller and call them out.







We ought believe NOTHING told to us by the race-supremacist state of Israel and the international enemies of the Palestinian people, least of all about their military and intelligence capabilities. It is interesting that you use the analogy of a pathogen invading a cell as a model for human warfare. Just as I no longer accept the germ theory of contagion, I no longer accept Israel's supposed intelligence superiority, for I know that the techno-military Machine will be defeated by organic uncontrollable Life.